How the Password Hash Synchronisation works?
Password Hash Sync copies a hash of a user’s password hash from on-premises AD to Microsoft Entra ID. This allows users to use the same password for both on-premises and cloud-based applications (like Microsoft 365), without sending the actual password or its direct hash to the cloud.
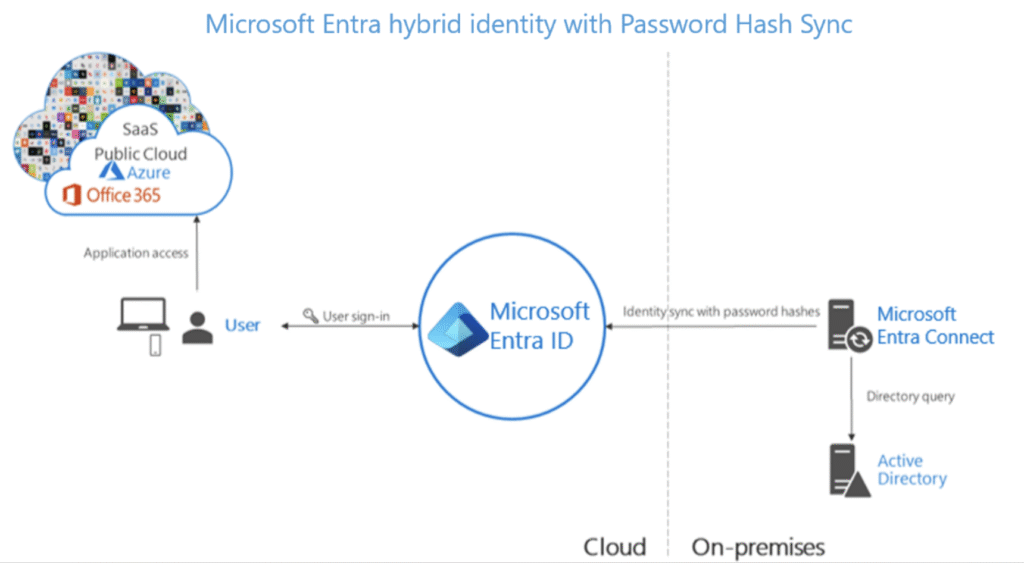
In Active Directory, passwords are stored as NT hashes (a cryptographic representation of the password).
Azure AD Connect (installed on-premises) reads the user’s NT hash from the AD database. It never reads the actual password.
Before sending it to the cloud, Azure AD Connect applies additional hashing:
- The NT hash is hashed again using PBKDF2 (Password-Based Key Derivation Function 2) with HMAC-SHA256.
- This extra hashing ensures that the hash stored in Entra ID is not the same as the one in AD.
- This prevents attackers from using the hash from the cloud to impersonate a user in AD.
Hash is sent securely to Entra ID
- The hashed hash (double-hashed value) is sent over a secure TLS connection to Microsoft Entra ID.
- It is then stored in Entra ID for authentication purposes.
When user sign-in to Entra ID integrated Applications,
This Content Is Only For Subscribers
- A user tries to log in to a Microsoft cloud service (e.g., Outlook, Teams).
- The entered password is hashed in the same way (using PBKDF2).
- Microsoft Entra ID compares the resulting hash with the stored value.
- If the hashes match, the user is authenticated.
How the Pass-through Authentication works?
Pass-through authentication (PTA) is a method of authentication that allows users to sign in to a service using their on-premises credentials (typically their Active Directory username and password) without the need to replicate password hashes to the cloud.
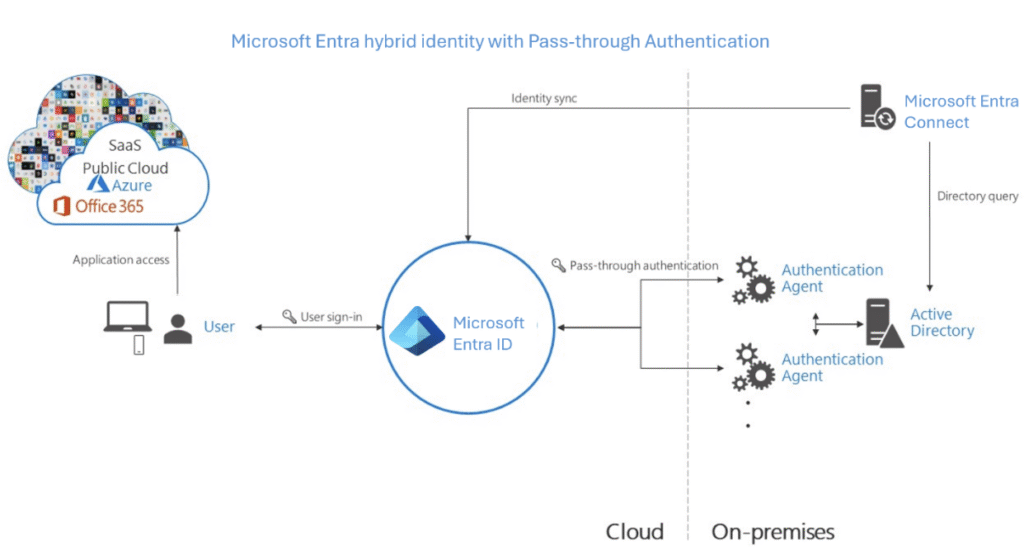
1. User Attempts to Sign In
- A user tries to log in to a cloud service like Microsoft 365.
- They enter their username and password on the cloud sign-in page (Azure AD)
2. Azure AD Receives Credentials
- Azure AD receives the credentials and determines that the user is configured to use pass-through authentication.
3. Azure AD Sends Encrypted Credentials
- Azure AD securely encrypts the user’s credentials and places them in a queue.
- This encrypted credential packet is waiting for an on-premises Authentication Agent to pick it up.
4. On-Prem Authentication Agent Picks It Up
- An Azure AD Pass-through Authentication Agent, running on a domain-joined server on-premises, listens for requests from Azure AD.
- The agent picks up the encrypted credentials from the queue.
5. Agent Authenticates User with Active Directory
- The agent decrypts the credentials.
- Then it attempts to authenticate the user directly against the on-premises Active Directory, using standard Kerberos or NTLM protocols.
6. Authentication Result Returned
- If authentication succeeds, the agent reports a success back to Azure AD.
- Azure AD then issues a token to the user to access the requested cloud service.
What is the difference between pass-through authentication and other authentication methods?
Below are the key difference with pass-through authentication with alternate options.
| Feature | PTA | Password Hash Sync (PHS) | Federation (e.g., ADFS) |
|---|---|---|---|
| Password stored in cloud | ❌ No | ✅ Yes (hashed) | ❌ No |
| Requires on-prem infra | ✅ Yes (Agent) | ❌ No | ✅ Yes (ADFS servers, etc.) |
| Complexity | Medium | Low | High |
| Real-time authentication | ✅ Yes | ❌ No (sync delay) | ✅ Yes |
How the Federated Authentication works?
ADFS (Active Directory Federation Services) is a Microsoft service that allows users to use their on-premises credentials (like AD username & password) to log into cloud services like Microsoft 365 — without storing or syncing passwords to the cloud
- User goes to Microsoft 365 login page (e.g.,
https://portal.office.com) - Enters
alice@company.com - Microsoft 365 (via Azure AD) detects that
company.comis federated - It redirects the user to ADFS on-premises (
https://adfs.company.com) - ADFS authenticates the user (via Active Directory)
- If successful, ADFS sends a SAML token back to Azure AD
- Azure AD accepts it and grants access to Microsoft 365 services
What are the Key difference with ADFS and other authentication methods?
| Method | Password in Cloud? | Needs On-Prem Infra? | Complexity | SSO Support |
|---|---|---|---|---|
| ADFS (Federation) | ❌ No | ✅ Yes | 🔺 High | ✅ Yes |
| Password Hash Sync | ✅ Yes (hashed) | ❌ No | ✅ Simple | ✅ Yes |
| Pass-through Auth | ❌ No | ✅ Yes (lightweight) | ⚖️ Medium | ✅ Yes |




