What is Certificate-based authentication in Entra ID?
Microsoft Entra identity certificate-based authentication (CBA) enables customers to allow or require users to authenticate directly with X.509 certificates against their Microsoft Entra identity, for applications and browser sign-in. CBA is supported only as a primary form of passwordless authentication.
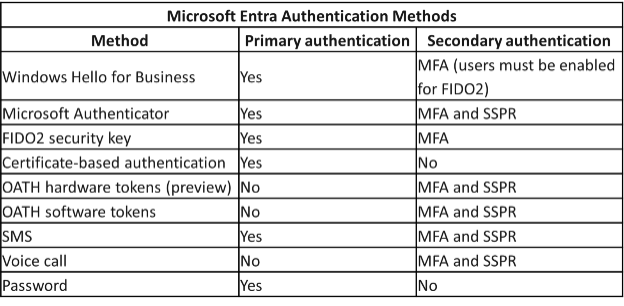
Explain the Entra ID authentication methods and which options are supported as Primary authentication methods?
Some authentication methods can be used as the primary factor when you sign in to an application or device. Other authentication methods are only available as a secondary factor when you use Microsoft Entra multifactor authentication or SSPR.
What is self-service password reset?
Self-service password reset (SSPR) is a feature of Microsoft Entra ID that allows users to change or reset their password, without administrator or help desk involvement. If a user’s account is locked or they forget or want to change their password, they can follow a prompt to reset it and get back to work. This ability reduces help desk calls and loss of productivity when a user can’t sign in to their device or an application.
What are the authentication methods available for SSPR?
When users register for SSPR, they’re prompted to choose the authentication methods to use.
- Mobile app notification
- Mobile app code
- Mobile phone
- Office phone
- Security questions
If they choose to use security questions, they pick from a set of questions to prompt for and then provide their own answers. Security questions can only be used during the self-service password reset (SSPR) process to confirm who you are, as a secondary form of authentication.
What is conditional access policy?
Conditional Access is a feature of Microsoft Entra ID that provides an extra layer of security before allowing authenticated users to access data or other assets. Conditional Access is implemented through policies that are created and managed in Microsoft Entra ID.
A Conditional Access policy analyses signals including user, location, device, application, and risk to automate decisions for authorizing access to resources (apps and data).
Conditional Access policies at their simplest are if-then statements. For example, a Conditional Access policy might state that if a user belongs to a certain group, then they’re required to provide multifactor authentication to sign in to an application.
What are the components of Conditional Access Policy?
A conditional access policy in Microsoft Entra ID consists of two components, assignments and access controls.
Assignments: When creating a conditional access policy, admins can determine which signals to use through assignments. The assignments portion of the policy controls the who, what, where, and when of the Conditional Access policy. All assignments are logically ANDed. If you have more than one assignment configured, all assignments must be satisfied to trigger a policy
Access Controls: When the Conditional Access policy has been applied, an informed decision is reached on whether to block access, grant access, grant access with extra verification, or apply a session control to enable a limited experience. The decision is referred to as the access controls portion of the Conditional Access policy and defines how a policy is enforced
What is Microsoft Entra Internet Access and Microsoft Entra Private Access?
Microsoft Entra Internet Access secures access to Software as a Service (SaaS) applications, including Microsoft Services, and public internet apps while protecting users, devices, and data against internet threats.
This Content Is Only For Subscribers
A Secure Web Gateway (SWG) is a cybersecurity solution that protects users from web-based threats by filtering internet traffic and enforcing security policies.
Microsoft Entra Internet Access provides an identity-centric Secure Web Gateway (SWG) solution for Software as a Service (SaaS) applications, including Microsoft Services, and other Internet traffic. It protects users, devices, and data from the Internet’s wide threat landscape with best-in-class security controls and visibility through Traffic Logs.
Microsoft Entra Private Access provides your users, whether in an office or working remotely, secure access to your private, corporate resources.
VPN solutions are often used as a primary method to control corporate network access. Once private network connectivity is established, the front door to your network is unlocked and on top of that, it’s common for users and devices to be over-permissioned. This significantly increases your organization’s attack surface.
Microsoft Entra Private Access can be deployed to block lateral attack movement, reduce excessive access, and replace legacy VPNs. The service provides your users – whether in an office or working remotely – secured access to your private, corporate resources.
What is Security Service Edge?
Microsoft Entra Internet Access and Microsoft Entra Private Access come together as a solution that converges Zero Trust network, identity, and endpoint access controls so that you can secure access to any app or resource, from any location, device, or identity. This type of solution represents a new network security category called Security Service Edge (SSE).
SSE helps address security challenges such as:
- The need to reducing the risk of lateral movement through a compromised VPN tunnel.
- The need to put a perimeter around internet-based assets.
- The need to improve service in remote office locations, such branch offices.
Explain the Target Resource option Global Secure Access and Authentication Context in CA Policy?
Global Secure Access (preview) – Global Secure Access is the unifying term used for both Microsoft Entra Internet Access and Microsoft Entra Private Access. Administrators can use conditional Access policies to secure the traffic that passes through the Global Secure Access service. This is done by defining traffic profiles in Global Secure Access. Conditional Access policies can then be assigned to the Global Secure Access traffic profile.
Authentication context – Authentication context can be used to further secure data and actions in applications. For example, users that have access to specific content in a SharePoint site may be required to access that content via a managed device or agree to specific terms of use.
What is the difference between Microsoft Entra RBAC and Azure RBAC?
Microsoft Entra built-in and custom roles are a form of RBAC in that they control access to Microsoft Entra resources. This is referred to as Microsoft Entra RBAC. In the same way that Microsoft Entra roles can control access to Microsoft Entra resources, Azure roles control access to Azure resources. This is referred to as Azure RBAC.
Although the concept of RBAC applies to both Microsoft Entra RBAC and Azure RBAC, what they control are different.
Microsoft Entra RBAC – Microsoft Entra roles control access to Microsoft Entra resources such as users, groups, and applications.
Azure RBAC – Azure roles control access to Azure resources such as virtual machines or storage using Azure Resource Management.
Explain access review and how you are using it in your environment?
Microsoft Entra access reviews enable organizations to efficiently manage group memberships, access to enterprise applications, and role assignment. Regular access reviews ensure that only the right people have access to resources.
With access reviews, admins can easily ensure that users or guests have appropriate access. Admins can ask the users themselves or a decision maker to participate in an access review and recertify (or attest) to users’ access. The reviewers can give their input on each user’s need for continued access based on suggestions from Microsoft Entra ID. When an access review is finished, you can then make changes and remove access from users who no longer need it.
What is Entitle Management?
Entitlement management is an identity governance feature that enables organizations to manage the identity and access lifecycle. Entitlement management automates access request workflows, access assignments, reviews, and expiration.





