What is Microsoft Entra ID?
Microsoft Entra ID, formerly known as Azure Active Directory or Azure AD, is an identity and access management solution from Microsoft that helps organizations secure and manage identities in cloud and on-premises environments.
Microsoft Entra ID provides user and group management, on-premises directory synchronization, reporting, self-service password changes for both cloud & On-Premises users, and single sign-on (SSO) across Azure, Microsoft 365, and many popular SaaS apps.
What is the difference between Entra ID and Entra Domain Services?
Entra ID protects identities and manages access to apps, devices, and data.
Entra Domain Services allows organizations to manage their domain controllers in the cloud.
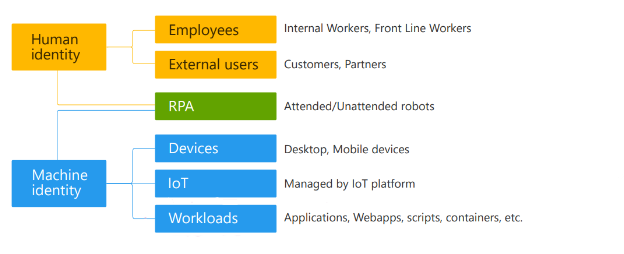
What are the Identity types in Microsoft Entra?
User identity and Machine identity are the 2 types of identities available in Microsoft Entra.
What is Entra External ID and Workload ID?
Microsoft Entra External ID provides external identities with secure access to any app. Azure AD B2B collaboration is now part of Microsoft Entra External ID as External ID B2B collaboration. Microsoft moving away from Azure AD B2B collaboration but the functionality are continued.
Microsoft Entra Workload ID help applications and services to access cloud resources securely. Workload identities are part of machine identities for software workloads, such as applications, services, scripts, or containers that require authentication and authorization as they access resources in cloud environments.
Just like users, a software workload needs an identity to access resources. Two common scenarios in Microsoft Entra today for workload identities are:
Managed identities: Used by developers to provision their service with access to an Azure resource such as Azure Key Vault or Azure Storage.
Application identities: Enable access to resources when IT admins or developers deploy apps in their environment.
This Content Is Only For Subscribers
What are the challenges with Workload Identity? How to solve the challenges?
Securing your workload identities is important because unlike a human user, a software workload may deal with multiple credentials to access different resources and those credentials need to be stored securely. It’s also hard to track when a workload identity is created or when it should be revoked. Enterprises risk their applications or services being exploited or breached because of difficulties in securing workload identities.
With Entra Workload Identities, we can strengthen the deployment of Zero Trust, empowering organizations to protect secrets, sensitive data, and other resources by
1. Securing access using Adaptive Conditional Access Policies
2. Setup identity protection for workload identity
3. Configure Access review for the workload identity provided with privileged roles.
What are the capabilities of Microsoft Entra ID?
Entra ID has set of comprehensive capabilities like,
App integrations and Sing sign-on: It helps to connect your workforce to all your apps from any location, using any device. Entra ID simplifies the app access from anywhere with SSO.
Passwordless and Multifactor Authentication: Help safeguard access to data and apps and keep it simple for users. Provide ease of use without the inherent risk of passwords by MFA.
Conditional Access: Apply the right access controls to strengthen your organization’s security.
Identity Protection: Protect identities and block identity attacks in real time.
Privileged identity management: PIM strengthen the security of your privileged accounts.
End user self service: Entra ID allows employees securely manage their own identity with self-service portals including My Apps, My Access, My Account, and My Groups.
Unified Admin center: Confidently manage all Microsoft Entra multicloud identity and network access solutions in one place.
What is Identity Secure Score?
Microsoft Entra ID includes an identity secure score, which is a percentage that functions as an indicator for how aligned you are with Microsoft’s best practice recommendations for security. Each improvement action in identity secure score is tailored to your specific configuration and the score is related to it.
Identity secure score available in all editions of Microsoft Entra ID, helps you to objectively measure your identity security posture, plan identity security improvements, and review the success of your improvements.
Examples of Best Practice recommendations are
- Minimize the Global Admin accounts
- Protect all users with risk policy
Most important: Check your organization’s secure score before the interview.
What is an Application and Service Principal in Entra ID?
Service Principal is an identity for an application. For an application to delegate its identity and access functions to Microsoft Entra ID, the application must first be registered with Microsoft Entra ID to enable its integration. Once an application is registered, a service principal is created in each Microsoft Entra tenant where the application is used. The service principal enables core features such as authentication and authorization of the application to resources that are secured by the Microsoft Entra tenant.
What are the types of groups available in Entra ID?
Groups are created to give access permissions to all members of the group, instead of having to assign access rights individually. There are 2 types of groups
Security: A security group is the most common type of group and it’s used to manage user and device access to shared resources. It is created for a specific security policy such as Self-service password reset or for use with a conditional access policy to require MFA.
Members of a security group can include users (including external users), devices, other groups, and service principals.
Creating security groups requires a Microsoft Entra administrator role.
Microsoft 365: A Microsoft 365 group, which is also often referred to as a distribution group, is used for grouping users according to collaboration needs. Microsoft 365 groups can give members of the group access to a shared mailbox, calendar, files SharePoint sites, and more.
Members of a Microsoft 365 group can only include users, including users outside of your organization.
Because Microsoft 365 groups are intended for collaboration, the default is to allow users to create Microsoft 365 groups, so you don’t need an administrator role.
What is Entra Cloud Sync?
Microsoft Entra Cloud Sync is designed to meet and accomplish your hybrid identity goals for the provisioning and synchronization of users, groups, and contacts to Microsoft Entra ID.
It accomplishes this by using the Microsoft Entra cloud provisioning agent. The agent provides a lightweight inter-directory provisioning experience that acts as a bridge between Microsoft Entra ID and Active Directory. An organization only needs to deploy the agent in their on-premises or IaaS-hosted environment
The Microsoft Entra Cloud Sync provisioning agent uses the System for Cross-domain Identity Management (SCIM) specification with Microsoft Entra ID to provision and deprovision users and groups.
What is OATH?
OATH (Open Authentication) is an open standard that specifies how time-based, one-time password (TOTP) codes are generated. One-time password codes can be used to authenticate a user. OATH TOTP is implemented using either software or hardware to generate the codes.
Software OATH tokens are typically applications. Microsoft Entra ID generates the secret key, or seed, that’s input into the app and used to generate each OTP.
OATH TOTP hardware tokens (supported in public preview) are small hardware devices that look like a key fob that displays a code that refreshes every 30 or 60 seconds. OATH TOTP hardware tokens typically come with a secret key, or seed, preprogrammed in the token. These keys and other information specific to each token must be input into Microsoft Entra ID and then activated for use by end-users.
OATH software and hardware tokens, are only supported as secondary forms of authentication in Microsoft Entra ID, to verify an identity during self-service password reset (SSPR) or Microsoft Entra multifactor authentication
What is password less authentication?
Many organizations planning to remove the use of passwords as part of sign-in events. When a user signs in with a passwordless method, credentials are provided by using methods like biometrics with Windows Hello for Business, or a FIDO2 security key. These authentication methods can’t be easily duplicated by an attacker.
Microsoft Entra ID provides ways to natively authenticate using passwordless methods to simplify the sign-in experience for users and reduce the risk of attacks.
Explain Windows Hello for Business?
Windows Hello for Business replaces passwords with strong two-factor authentication on devices. This two-factor authentication is a combination of a key or certificate tied to a device and something that the person knows (a PIN) or something that the person is (biometrics). PIN entry and biometric gesture both trigger the use of the private key to cryptographically sign data that is sent to the identity provider. The identity provider verifies the user’s identity and authenticates the user.
What are the benefits of Windows Hello for Business?
Windows Hello for Business helps protect against credential theft, because an attacker must have both the device and the biometric info or PIN, making it more difficult to gain access without the employee’s knowledge.
As a passwordless authentication method, Windows Hello for Business serves as a primary form of authentication. In addition, Windows Hello for Business can be used as a secondary form of authentication to verify an identity during multifactor authentication.
What is FIDO2 and what is the use of it ?
Fast Identity Online (FIDO) is an open standard for passwordless authentication. FIDO allows users and organizations to leverage the standard to sign in to their resources using an external security key or a platform key built into a device, eliminating the need for a username and password.
FIDO2 is the latest standard that incorporates the web authentication (WebAuthn) standard and is supported by Microsoft Entra ID. FIDO2 security keys are an unphishable standards-based passwordless authentication method that can come in any form factor. These FIDO2 security keys are typically USB devices, but could also be Bluetooth or Near Field Communication (NFC) based devices, which are used for short-range wireless data transfer. With a hardware device that handles the authentication, the security of an account is increased as there’s no password that could be exposed or guessed.





