What is Microsoft Entra Connect?
Microsoft Entra Connect is a solution that bridges an organizations on-premises Active Directory with your cloud-based Microsoft Entra ID. IT can synchronize identities from on-premises into Azure and ensures a consistent identity across both platforms. This connection enables services like password hash synchronization, pass-through authentication, and seamless single sign-on (SSO).
What are the capabilities of Entra Connect?
Microsoft Entra Connect is the Microsoft tool designed to meet and accomplish your hybrid identity goals. It provides the following capabilities:
- Synchronization – Responsible for creating users, groups, and other objects. Then, making sure identity information for your on-premises users and groups is matching the cloud. This synchronization also includes password hashes.
- Password hash synchronization – A sign-in method that synchronizes a hash of a user’s on-premises AD password with Microsoft Entra ID.
- Pass-through authentication – A sign-in method that allows users to use the same password on-premises and in the cloud, but doesn’t require the extra infrastructure of a federated environment.
- Federation integration – Federation is an optional part of Microsoft Entra Connect and can be used to configure a hybrid environment using an on-premises AD FS infrastructure. It also provides AD FS management capabilities such as certificate renewal and more AD FS server deployments.
- Health monitoring – Microsoft Entra Connect-Health provides robust monitoring.
What are the cloud authentication options available in Entra ID?
Password hash synchronization & Pass-through authentication are the 2 cloud authentication methods in Entra ID.
PHS – The simplest way to enable authentication for on-premises directory objects in Microsoft Entra. Users can use the same username and password that they use on-premises without having to deploy any more infrastructure.
PTA – Provides a simple password validation for Microsoft Entra authentication services by using a software agent that runs on one or more on-premises servers. The servers validate the users directly with your on-premises Active Directory, which ensures that the password validation doesn’t happen in the cloud.
Companies with a security requirement to immediately enforce on-premises user account states, password policies, and sign in hours might use this authentication method.
What is Federated Authentication?
When you choose this authentication method, Microsoft Entra ID hands off the authentication process to a separate trusted authentication system, such as on-premises Active Directory Federation Services (AD FS), to validate the user’s password.
The authentication system can provide other advanced authentication requirements. Examples are smartcard-based authentication or third-party multifactor authentication.
What is a Source Anchor?
The source Anchor attribute is defined as an attribute immutable during the lifetime of an object. It uniquely identifies an object as being the same object on-premises and in Microsoft Entra ID. The attribute is also called immutableId and the two names are used interchangeable. The attribute is used for the following scenarios:
When a new sync engine server is built, or rebuilt after a disaster recovery scenario, this attribute links existing objects in Microsoft Entra ID with objects on-premises.
If you move from a cloud-only identity to a synchronized identity model, then this attribute allows objects to “hard match” existing objects in Microsoft Entra ID with on-premises objects.
If you use federation, then this attribute together with the userPrincipalName is used in the claim to uniquely identify a user.
What is the staging server?
Microsoft Entra Connect supports installing a second server in staging mode. A server in this mode reads data from all connected directories but doesn’t write anything to connected directories. It uses the normal synchronization cycle and therefore has an updated copy of the identity data.
How Entra Connect works?
The provisioning engine connects to each Active Directory Forest and to Microsoft Entra ID.
The process of reading information from each directory is called Import. Export refers to updating the directories from the provisioning engine.
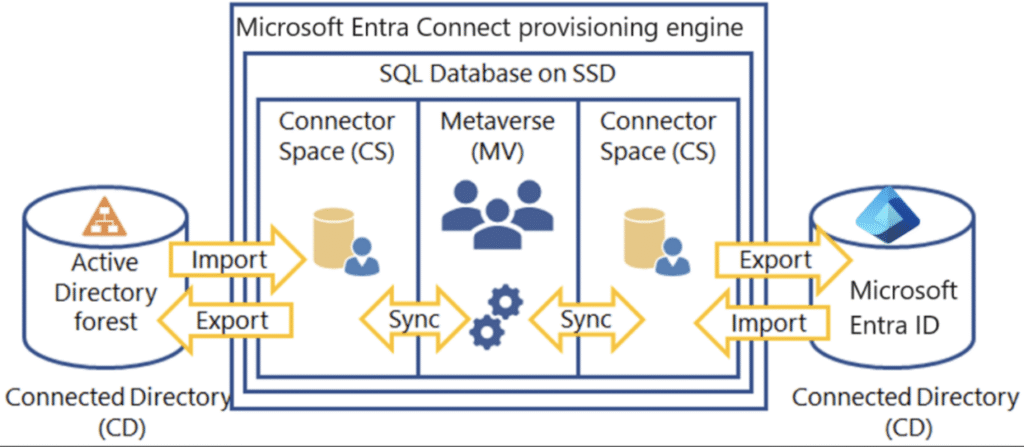
Sync evaluates the rules of how the objects will flow inside the provisioning engine.
What is connector space and metaverse?
Connector Space (CS) – Objects from each connected directory (CD), the actual directories, are staged here first before they can be processed by the provisioning engine. Microsoft Entra ID has its own CS and each forest you connect to will have its own CS.
Metaverse (MV) – Objects that need to be synced are created here based on the sync rules. Objects must exist in the MV before they can populate objects and attributes to the other connected directories. There’s only one MV.
What is Microsoft Entra Cloud Sync?
Microsoft Entra Connect cloud sync is designed to accomplish hybrid identity goals for synchronization of users, groups and contacts to Microsoft Entra ID. The synchronization is accomplished by using the cloud provisioning agent instead of the Microsoft Entra Connect application. It can be used alongside Microsoft Entra Connect sync.
What are the Risk Types identified by Entra Identity Protection?
Below are the Risks detected by Identity Protection in Entra.
| Risk detection type | Description |
| Anonymous IP address | Sign in from an anonymous IP address (for example: Tor browser, anonymizer VPNs). |
| Atypical travel | Sign in from an atypical location based on the user’s recent sign ins. |
| Malware-linked IP address | Sign in from a malware-linked IP address. |
| Unfamiliar sign in properties | Sign in with properties we’ve not seen recently for the given user. |
| Leaked credentials | Indicates that the user’s valid credentials have been leaked. |
| Password spray | Indicates that multiple usernames are being attacked using common passwords in a unified brute-force manner. |
| Microsoft Entra threat intelligence | Microsoft’s internal and external threat intelligence sources have identified a known attack pattern. |
| New country | This detection is discovered by Microsoft Defender for Cloud Apps (MDCA). |
| Activity from anonymous IP address | This detection is discovered by MDCA. |
| Suspicious inbox forwarding | This detection is discovered by MDCA. |
What is Defender for Identity and are you using it in your environment?
Microsoft Defender for Identity (formerly Azure Advanced Threat Protection, also known as Azure ATP) is a cloud-based security solution. Defender for identity uses your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization. Defender for Identity enables SecOp analysts and security professionals struggling to detect advanced attacks in hybrid environments to:
- Monitor users, entity behavior, and activities with learning-based analytics
- Protect user identities and credentials stored in Active Directory
- Identify and investigate suspicious user activities and advanced attacks throughout the kill chain
- Provide clear incident information on a simple timeline for fast triage
Currently we are not using Defender for Identity solution and our security team using different 3rd party tools for this functionality.



